RapidIdentity Server
Do not install RapidIdentity Server on the same server running Microsoft SharePoint.
Ensure the RapidIdentity Server host meets or exceeds the minimum requirements listed below.
Microsoft® Windows Server 2012 R2 or greater
RapidIdentity may be deployed to servers operating as domain controllers or member servers; however, it is not recommended to deploy on a domain controller if possible
RapidIdentity may be deployed to physical servers, virtual servers, or both
IIS 7.0 or higher
Microsoft SQL Server or SQL Express 2014 or higher
Dual core Pentium compatible 2GHz processor or faster per core
4GB RAM (8GB if SQL is installed on the same server)
.NET Framework 4.7.2 or greater
120 MB of available hard disk space for RapidIdentity Server
Ports 80 and 443 (when using SSL) must be allowed through any firewall where communication to RapidIdentity Server is required
Ports 2195, 5228, 5229, 5230 and 443 (TCP and UDP) are required for communication when using PingMe
Ports 1812 and 1813 (UDP) are required for RADIUS (only needed if installing Network Policy Server (NPS) on the same server, for example, to accommodate OTP to VPN authentication or for a number of other integration points)
Ports 1433 is required for SQL Communication
NPS with RADIUS and OTP Authentication
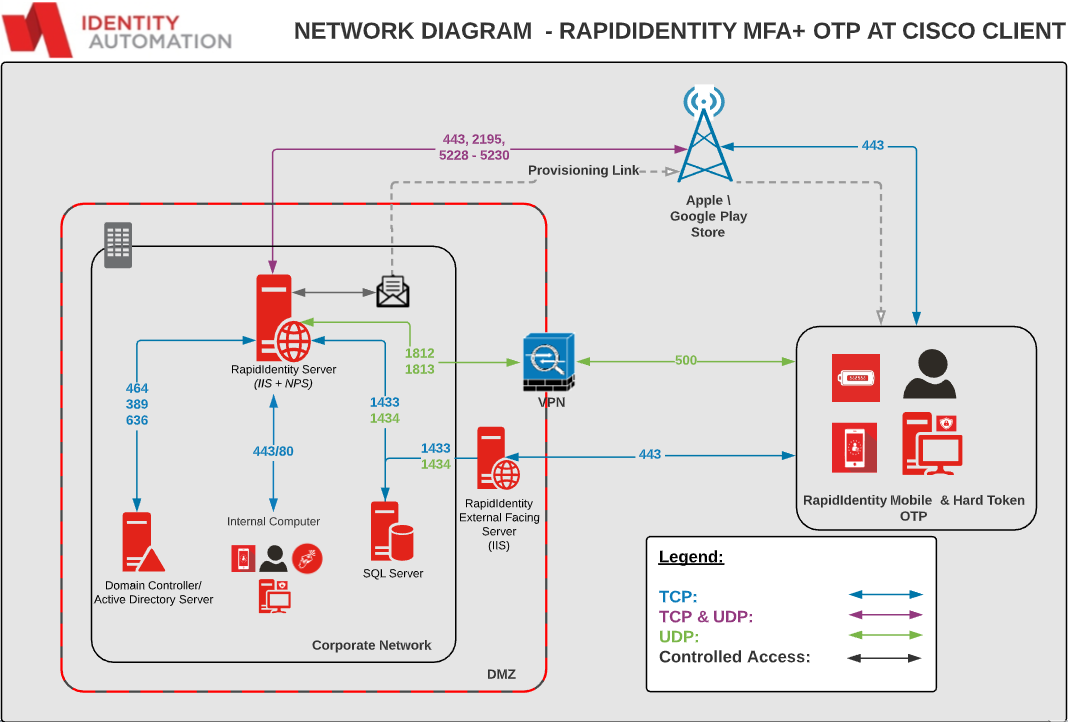
RapidIdentity MFA+ can be leveraged as an authentication method for Virtual Private Networks and other 3rd party applications that can utilize RADIUS authentication with MS-CHAPV2 (Preferred) or PAP protocols.
Below is a diagram of a sample environment that depicts network traffic with MFA+ acting as a RADIUS proxy.
 |
Note
MFA+ Supports One-Time Passwords and Push notifications from the RapidIdentity Mobile applications as well as One-Time Password hard tokens.
Configuring Radius\NPS Support
Prior to configuring Radius\NPS Support, ensure that these three items are present.
Visual C++ Redistributable for Visual Studio 2015, 2017, and 2019 must be installed.
Important
This dependency is not installed by the RapidIdentity Server installation process.
Ensure the Network Policy Server (NPS) is installed on the same server as RapidIdentity Server.
NPS should be configured for appropriate policies with whatever Radius clients need to leverage this server for Radius authentication.
The specifics on how to configure NPS along with anything associated with RADIUS are beyond the scope of this installation guide.
Organizations should evaluate internal policies prior to completing the Radius\NPS Support with RapidIdentity Server.
Details on configuring various RADIUS clients can be obtained through Microsoft or Identity Automation Support.
After configuring NPS specific to the organization, follow these four steps to configure Radius\NPS Support in RapidIdentity Server.
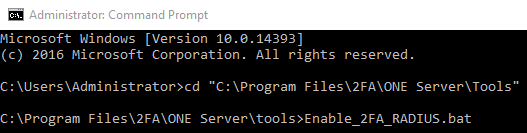
Open a Command Prompt window as an Administrator.
Navigate to C:\Program Files\2FA\ONE Server\Tools.
Type Enable_2FA_RADIUS.bat and press ENTER.
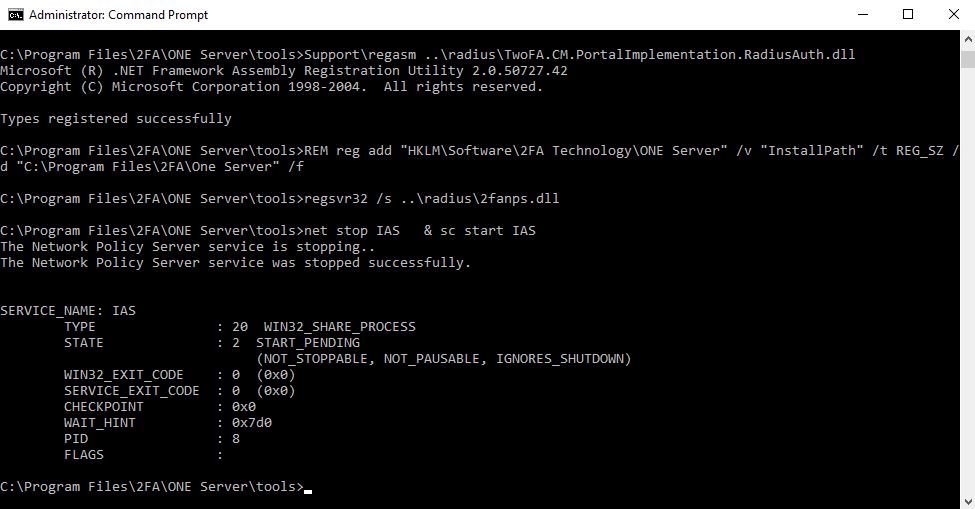
Upon completion, the following information will display.
After enabling the RADIUS.bat file it is necessary to configure NPS to communicate with the organizational VPN software or other third party software in order to use RapidIdentity Server with that solution.