Custom Registry Strings and Values
These registry entries and values may not be present until an event occurs or until the setting is added manually.
If RapidIdentity Windows Client is configured to synchronize with RapidIdentity Server, these registry values appear if a policy is pushed to RapidIdentity Windows Client.
Value Name | Value Type | Value | Description | Example | |
|---|---|---|---|---|---|
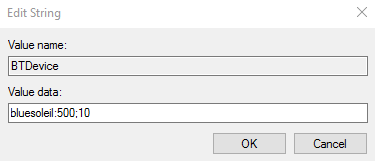
BTDevice | String | bluesoleil:500;10 | This String corresponds to the Bluetooth device software driver name (bluesoleil), the period in milliseconds between signal checks (500), and the number of checks over which the signal is averaged (10: default). The numeric values can be adjusted as needed to ensure optimal performance. |
| |
BTLocktime | DWORD | 0, 1, 2, or 3 | This setting corresponds to the choice dropdown menu position, such as Prompt with keypress being in first position (value = 0). | 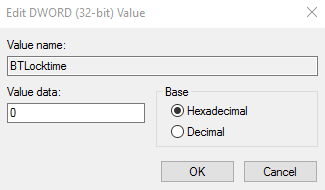 | |
BTLockPromptTime | DWORD | 15 (seconds) | This setting corresponds to the number of seconds users have to authenticate once the workstation detects the Bluetooth device. | 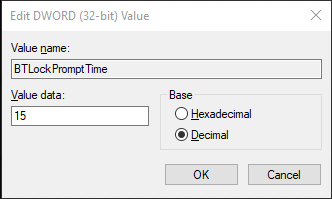 | |
ServiceUrl | String | URL | This String is not present until the RapidIdentity Windows Client Server URL is set either in the installer or within the application. The value should be entered exactly as defined in the example: | 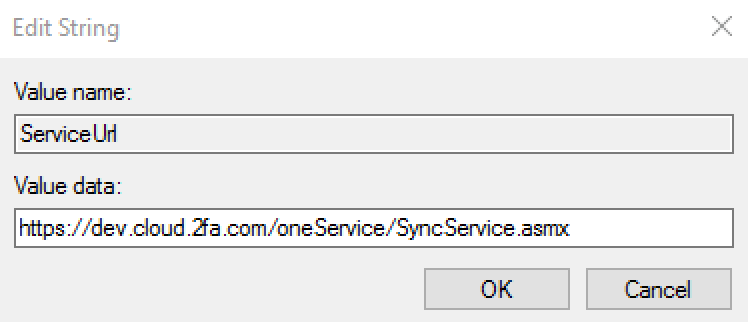 | |
ServiceTimeout | DWORD, hexadecimal | 20,000 (default) | This setting allows extra time for RapidIdentity Windows Client to synchronize with RapidIdentity Server over slow network connections. The timeout value is in Milliseconds. If not configured, the default value is 20,000 (20 seconds). | 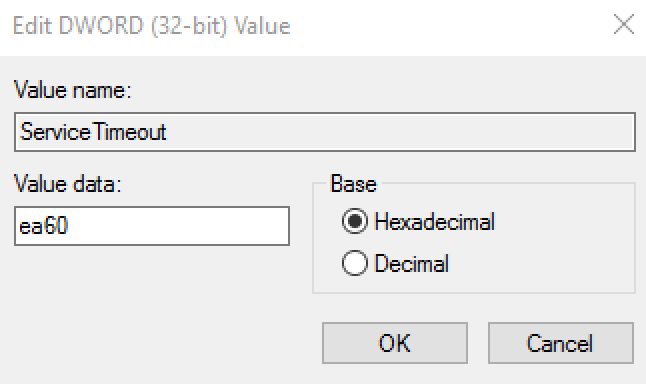 | |
SuppressSplashScreen | String | Boolean | This setting is designed to suppress the blue RapidIdentity Windows Client splash screen that informs the user that an operation is in progress. The value should be entered True to suppress the splash screen and False to enable the splash screen. In the absence of the registry string and value, the splash screen will be enabled. | 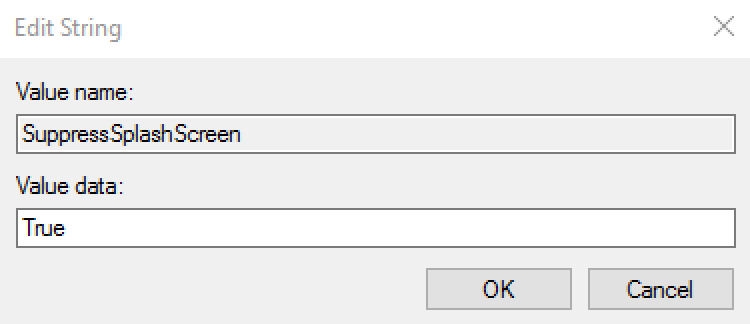 | |
EnrollmentStation | String | Boolean | This setting is to limit the amount of data stored locally and reduce the amount of synchronization that occurs between an enrollment Workstation and Server. This setting is useful to organizations that choose to have users enroll at a central badging or enrollment station. Following enrollment, the user would effectively not require access to the system except when replacing their badge. This setting also prevents the syncing of data down to the local system when enrolling through RapidIdentity Server. The value should be entered True to turn the standard installation into an Enrollment Station and False to revert back to a standard system. For installations that are not enrollment stations, it is expected that synchronization process time will increase as more and more users are added to the local workstation. | 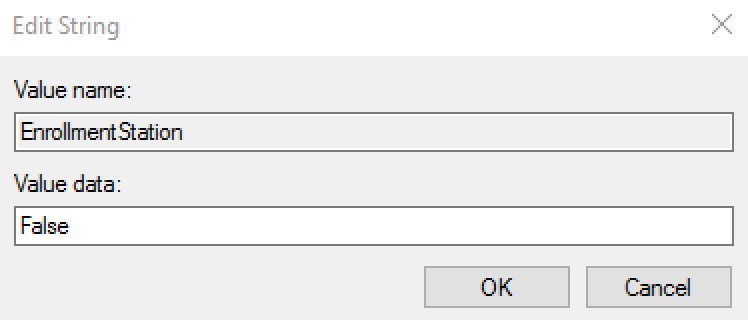 | |
LogLevel | DWORD | 0 (default) | The purpose of this setting is to log RapidIdentity Windows Client activities with the intent to perform advanced troubleshooting. This string will only be created following a request from the Identity Automation Support Team, however, the log file output can also be useful for administrators with advanced knowledge of RapidIdentity Windows Client. To turn on application logging, add the registry string manually and use these.
Once the registry entry is created, a log file named log.txt appears in the logs folder: C:\Program Files\2FA\ONE\Client\logs. If logging is not stopped, the log file will continue to grow until it reaches 10 MB in size, at which time a second log.txt file will be automatically created. | 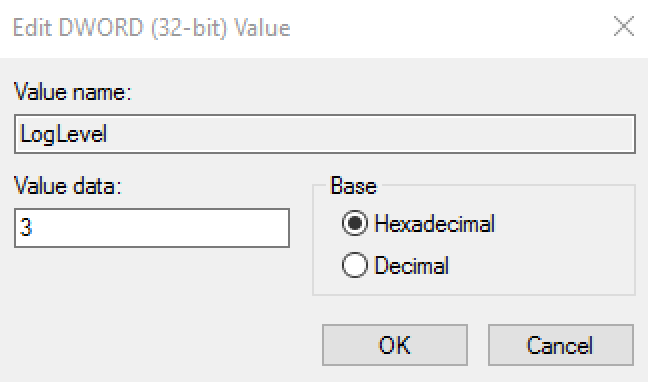 | |
SuppressAppUI | SuppressAppUI | Boolean | The purpose of this setting is to prevent the RapidIdentity Windows Client UI from being executed locally and is similar to the feature provided during the installation of RapidIdentity Windows Client called Hide Executable. The differences between SuppressAppUI and Hide Executable are that SupressAppUI does not remove the RapidIdentity Windows Client icon from the desktop nor does it affect any RapidIdentity Windows Client entries in the Programs Menu. Once suppressed, users will not be able to enroll or perform any function within the local RapidIdentity Windows Client application, but will have access to the GINA and Credential Providers within RapidIdentity Windows Client. The Taskbar Icon will also be available to users. All lifecycle events previously performed in RapidIdentity Windows Client will either need to be performed within the GINA/Credential Provider or through RapidIdentity Server. The value should be entered True to suppress the UI and False to enable the UI. | 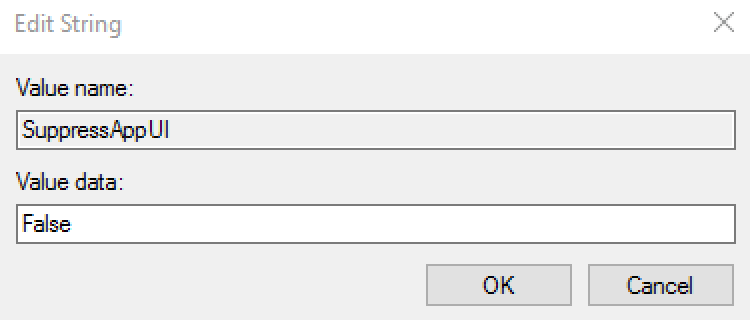 | |
EnableRFIDeas | String | True | This setting is to enable the use of RFIDeas pcProx and pcProx Plus series 82 card readers to be used by RapidIdentity Windows Client. The value of this string should be set to “True” to enable support. On 64-bit operating systems, if 32-bit Internet Explorer is to be used for access to the RapidIdentity Windows Client User or Administrator’s portal to issue or manage cards using an RFIDeas pcProx reader, a second registry setting is required. The same String Value, EnableRFIDeas="True" must be present in the HKLM | Software | Wow6432Node | foray registry. This String value is not required for 64-bit Internet Explorer, or for supporting RFIDeas outside of the RapidIdentity Windows Client web portals. | 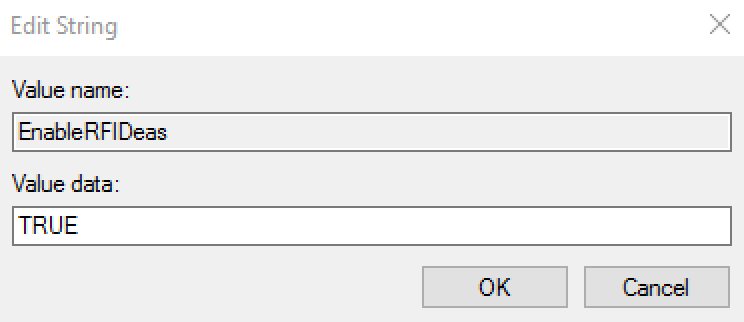 | |
SAAccessInterval | DWORD, hexadecimal | 10 (seconds, default) | This setting configures the amount of time, in seconds, between initial detection of a Secured Application and subsequent detection of the same instance of the application. This feature allows for slow application authentication times where Secured Applications would otherwise detect the same authentication screen multiple times during a single authentication process. Provide an interval value as required. The default setting is 10 seconds. | 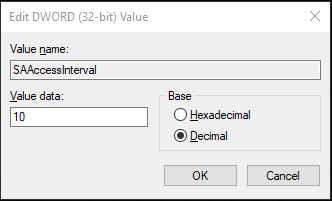 |
FIDO service is also installed during this process. The registry information for this is as follows:
HKEY_LOCAL_MACHINE\SOFTWARE\Identity Automation\FIDOServiceNote
There are special characters for each entry (>, @).
BindingRequest: reg_sz: >tcp://localhost:6215BindingResponse: reg_sz: @tcp://*:6215ResponseTimeout: reg_dword = 5Note
This value represents seconds.
Risk-Based Authentication
Risk-based Authentication includes a software token element comprised of a number of factors that may include network information, user information, positive device identification (e.g. device forensics, user pattern analysis, and user binding), user profiling, and high-risk challenge/response questions.
RapidIdentity Windows Client can adhere to regulatory compliance that requires risk-based authentication as described above.
By combining elements to securely and uniquely identify an authentication method used by a specific user on a specific device, policies may be enforced that contain logic as to the authentication method available for that user. Typically, this involves calculating a grace period on a specific device whereby a user may authenticate with a username and password, or whether that user must use another form of advanced authentication.
When a user attempts to authenticate without using an advanced authentication method, the RBA policy notifies the user that an advanced authentication method must be used.
The user’s authentication options are presented with available advanced authentication options.
Both of the Risk-Based Authentication registry value names must be entered and configured manually.
Value name | Value Type | Value | Description | Example |
|---|---|---|---|---|
RBATimeout | String | 0 | The purpose of this setting is to configure the grace period (in days) used by RapidIdentity Windows Client’s Risk-Based Authentication to allow for login by username and password. Once this grace period has been met, the user must authenticate using an advanced authentication method. The value of this string should be set to “0” to always enforce advanced authentication, or to any other number. | 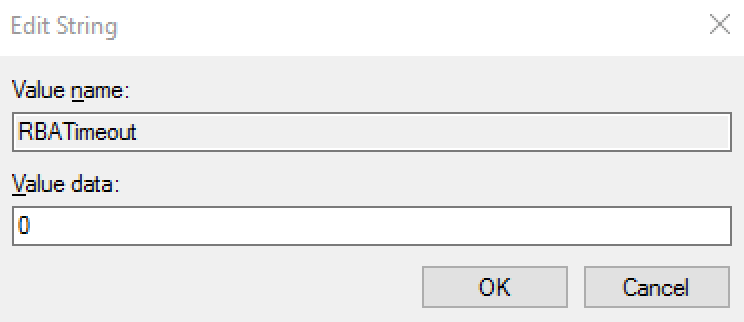 |
RBA | String | True | The purpose of this setting is to enable the use of RapidIdentity Windows Client’s Risk-Based Authentication. RBA enforces the use of an advanced authentication method, whereby authentication with username and password is only allowed during a specified grace period. | 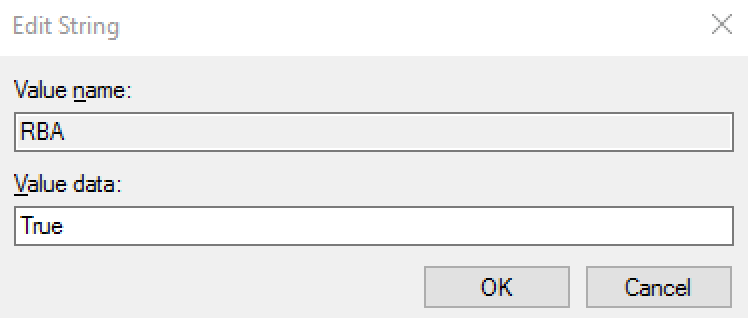 |